My big, fat, self-assigned new project — or, as I like to call it, the bug up my butt — is system roll-outs. That is, I realized at some point two things. One, I am managing way more computers than ever before, and way more than I realized; and two, the scope and variety of these various systems has become increasingly wide. These realizations inevitably brought me crashing, headlong (yes, headlong) into a third and final revelation: I need to come up with a better system for managing machine builds and systems roll-outs.
Enter: NetBoot.
Actually, let me first explain how we've handled this in the past. When I began this job we had maybe 15-20 Macs running OS 9 briefly, and then OS X since about its inception. Mac OS 9 was notoriously easy to build. Just copy that shit and be done with it. But Mac OS X was a different beast entirely. Mac OS X was complicated. Moody. A tougher nut to crack. Mac OS X required me to delve into the dark arts of system cloning.
Cue thunder clap, scary music.
The process that eventually evolved was cloning over firewire. We'd build our master machine — a basic Mac OS install with all the latest updates and our requisite software — and then clone that to the other machines over firewire, with clients booted into our Master via firewire target disk mode. This was a quick and dirty way to build a bunch of systems. Once the group was built we could customize machines or groups of machines as we saw fit. For a lab of 15-20 Macs this has worked swimmingly. But our lab has grown slowly and steadily, and completely without my realizing it.
My latest count shows our lab at more like 50 Macs now. We've added a bunch of stuff: laptops, servers, more A/Vmachines of various configurations, a render farm, and of course more workstations. Using our old system of firewire cloning is becoming increasingly clumsy, slow and error-prone. We need a better way of doing things.
Okay, now. Enter: NetBoot!
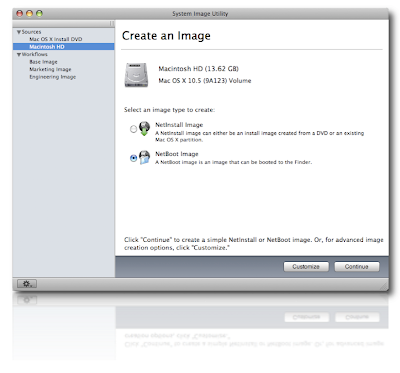
Leopard's NetBoot Interface<
(click image for larger view)
NetBoot is Mac OS X Server technology that allows for centralized storage of and access to system images for installation over the network. The way it works is this: You build a system, trick it out, make it perfect — this is your Master System. Put it on a firewire drive or something transportable, because you can't be booted from your Master System for the next series of steps — imaging. Run the application called System Image Utility, that comes with Mac OS X Server's server tools, and create a NetInstall image from your Master System. Load that image onto your server and enable it in the NetBoot settings in Server Admin. And what happens next is something akin to magic (unless you use Linux, and then it's pretty par for the course, I guess.)
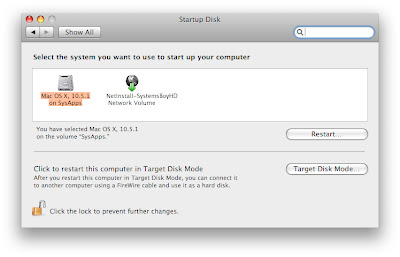 The Network Boot Volume: So That's What It's For!
The Network Boot Volume: So That's What It's For!>
(click image for larger view)
With your NetInstall image enabled on your server, go to any client system and open the Startup Disk Preferences. Where you'd normally see the "Network Startup" icon (I'll bet you always wondered what that was for), you'll now get something a bit more descriptive. You should now be given the opportunity to boot from your master image. Choosing to do so will incur further magical results. Your system will now boot... Over the network! What's even cooler is that you'll be booted into the same basic installer environment you'd see if you were booted off a Mac OS X install disc, and you'll be walked through the steps required to install your Master System onto your computer. Um... OVER THE NETWORK!
There are some immediate advantages to a system such as this. First off, you can have a bunch of different Master System images for various build configurations in your lab. For instance, we can have a separate build for laptops and desktop machines. Cool! Also, this can all be automated (thanks to Automator integration) to make the process run almost entirely unattended. Sweet! And since the whole thing sits on the server and is available at all times, if a machines needs a rebuild, you just set it and forget it. Awesome!
But NetBoot has its drawbacks as well. Images — particularly large images — take for-freaking-ever to build. To give you an idea of how long, my near-36GB boot drive took an hour or so to clone to firewire, then 3-4 hours to be imaged by System Image Utility. So each build will take several hours to create. And God help you if you make a mistake on one of your images: the NetInstall images are read-only and can't (to my knowledge) be modified once they're built. NetInstall technology can't be used for non-package installers or updates either (again, to my knowledge), so you'll have to run all your Adobe and Microsoft updates by hand as usual. Also, one minor caveat that threw me at the outset: Mac OS X 10.5 server can only serve Mac OS X 10.5 builds. So you'll either be needing to update everything to Leopard or wait until your server and client OSes match.
I think I'm right on the crux of really needing this. I could probably live without it. Keep doing what I'm doing. But I do think I'm at a point where the benefits of using NetBoot outweigh its limitations. And I have enough resources now (like the required massive drive space and robust stable servers) that it's not impractical on the physical level. So, this summer I plan to use NetBoot to build my lab.
I mean, imagine this: you get your new systems over the summer, you unbox them, plug them into your network, set them to NetBoot (everybody say "command-n"! Good!) and go home for the night. You come in the next day and everything's basically done. You've just built your lab. Overnight. In your sleep. I don't know. Sounds pretty cool to me.
I'll let you know how it goes.
Oh, and by the way, in case you can't tell, I'm just now learning all this. It's still very new to me and there is a lot about it I don't know. So if anyone has any experiences or insights into using NetBoot (or if I get any of the facts wrong), I would absolutely love to hear about it. Please feel free to share your experiences in the comments.